Beginning Thursday, February 26, 2026, at 4:30 p.m., the Office of Information Security will restrict access to certain apps and websites through the Clemson Guest network. The increased security measures will not impact users and devices connected to eduroam. This update is part of ongoing efforts to secure and safeguard Clemson’s networks and systems.
CCIT News and Notices
Additional apps will now require 2FA when logging in
CCIT is expanding two-factor authentication (2FA) to additional third-party applications. Some apps that did not previously require 2FA may now prompt users to authenticate after logging in with a Clemson username and password. This change is part of an ongoing effort to better protect Clemson accounts, personal information and systems from unauthorized access.
Two-factor authentication methods like Duo Mobile are already widely used across many Clemson services, so most users should be familiar with this process. Expanding 2FA to more applications helps provide consistent, reliable protection across University systems.
CCIT This Week: Update your Duo Mobile app before Feb. 2; beware of “browser in the browser” tricks; learn a new skill with Percipio
Week of January 26, 2025

Welcome to CCIT This Week, where we give you a rundown of news, events, tips and more. Follow us on social media for information and timely updates.
News
After February 2, the Duo Mobile app will not work for users who have not updated to version 4.85 or newer. Students, faculty and staff should ensure their app is up-to-date to avoid losing access to Clemson systems. Instructions to update your Duo Mobile app are available on the CCIT blog.
There has been an increase in cybercriminals using the Browser in the Browser (BitB) trick to steal login and password information. This trick has become more common on social media platforms such as Facebook and Instagram, but it can be used in any environment that uses a login page.
Events
Research, Computing and Data will host workshops this semester! Join the RCD team and expand your knowledge of high-performance computing and research resources available to you. The next workshop is “Introduction to Nextflow” on Tuesday, January 27 at 11 a.m. Registration is required; open to all Palmetto users.
The popular GIS Fundamentals Workshop Series continues this week! This 6-workshop series held on Friday mornings is streamlined to cover the GIS fundamentals; no prior experience is necessary. In-person sessions began January 16 or join online sessions starting February 27. Note: Attendance at the first two workshops is mandatory to participate in the remaining sessions.
January Tech Tip
A great New Year’s resolution: learn a new skill! Clemson faculty and staff have free access to Percipio, which offers thousands of courses, books, audiobooks and more to boost your professional development in a wide range of topics.
Keep Duo Mobile app updated to maintain access to Clemson systems
Clemson University uses the Duo Mobile two-factor authentication (2FA) app to ensure security and privacy of University information and systems. Beginning February 2, Duo is ending support for older versions of the Duo Mobile app to improve security and performance. After this date, versions of the Duo Mobile app earlier than version 4.85 will not work to access Clemson University systems that require 2FA.
Any app that is not updated by February 2 will lose the ability to authenticate and users will be locked out of Clemson services such as Canvas, iROAR, VPN and Kronos.
To continue accessing Clemson systems that require 2FA, faculty, staff and students must update the Duo Mobile app or set up an alternate authentication method.
What to do:
- Check your device. Phone must meet these minimum requirements to support the latest version of Duo Mobile:
- Apple devices: Go to Settings > General > About > iOS Version. Verify iOS 16 or higher.
- Android devices: Go to Settings > About Phone > Android Version. Verify Android 11 or higher.
- Update the Duo Mobile app.
If a phone can’t upgrade to at least iOS 16 or Android 11, other options are:
- Using another smartphone or tablet that meets requirements for Duo Mobile.
- Contacting the CCIT Support Center to discuss and set up other authentication options such as:
- Platform authenticators like Windows Hello or Apple TouchID
- Passkeys in password managers like Keeper, 1Password or Google Password Manager
- Hardware token ($20 cost)
Updating now ensures uninterrupted access to Clemson systems.
If faculty, staff or students have questions, need help updating or their device cannot be upgraded, visit the CCIT Support Center on the second floor of Cooper Library, email ithelp@clemson.edu or call (864) 656-3494.
Browser in the Browser (BitB) Trick
There has been an increase in cybercriminals using the Browser in the Browser (BitB) trick to steal login and password information. This trick has become more common on social media platforms such as Facebook and Instagram, but it can be used in any environment that uses a login page.
The BitB trick uses hidden code to create a fake pop-up looking window in your browser with a login prompt. Because the fake pop-up is entirely generated, it can include a convincing-looking address bar at the top that displays correct domain names. This trick can easily fool users who are looking at the URL before entering their credentials. For example, the BitB trick could be showing what looks like a pop-up window for a Google login and include the correct google.com address as well as all of the correct graphics and formatting. After entering your credentials, the user may even be redirected and logged into the official website. But through this process, the cybercriminal also collected and saved the user’s login and password information, which they can use themselves later. Most login pages are static single pages and do not typically have their login screen in a pop-up window. One of the best ways to spot this BitB trick is that the pop-up window cannot be moved outside of the original main browser window.
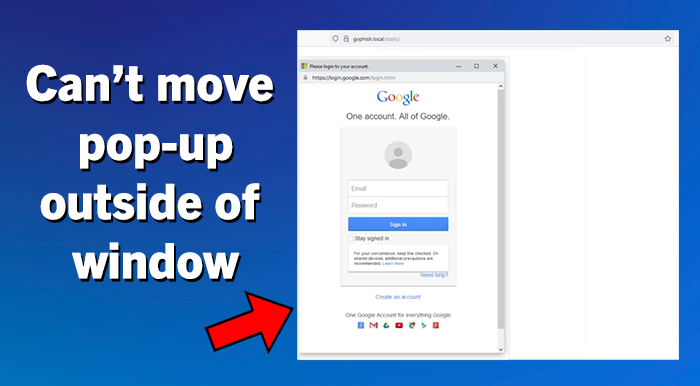
Ways to Avoid the BitB trick:
- For logging into any account, don’t trust a button, page link or email link.
Instead, navigate to the site’s official website URL in a separate browser tab to login. - If you are prompted to enter credentials into a login pop-up window, first check to see if the pop-up window can move outside of the browser window. Essential for the BitB trick, are iframes, which are connected to the underlying browser window and cannot be pulled outside it.
- It is also recommended to use Two Factor Authentication on any account, when available, to give you an extra layer of protection.
“Do I Keep My Email?” And Other Tech Questions From Graduating Tigers
Graduation is an exciting time for every Tiger, but it unfortunately does mean a change to some of the software and services you’ve grown accustomed to during your time at Clemson. Luckily, with a few minutes of review, you can prepare your technology and data for graduation.
Frequently Asked Questions
Do I keep my Clemson Google account?
Graduates will have access to their Clemson Google account for one year following graduation. Please note that forwarding of your @clemson.edu email address will cease soon after your username is deactivated. We suggest updating your contacts or accounts to use a different email address so you don’t lose anything when your account is closed.
We recommend you move your Google Drive files to another cloud storage service or personal Google Drive account in preparation for the closure of your Clemson Google account after one year. You can use Google Takeout (takeout.google.com) to export your Google account data if you wish to store it elsewhere, or you can use the transfer service (takeout.google.com/transfer) if you plan to move it to another Google account.
What about the files in my other cloud storage accounts?
- Your access to Box and OneDrive will end one year after graduation. We recommend that you download your files from those accounts as soon as possible, so you don’t forget about them.
- Any files you create and manage in CUapps (Citrix) are stored on your U: drive (also called Home Directory). You will have access to your U: drive for one year after graduation, so be sure to download those files before you lose them. The CCIT Knowledge Base contains instructions to access your U: drive for macOS and Windows.
- If you use the Palmetto Cluster or any of Clemson’s research computing storage, we recommend you download your data from there as well. For research computing assistance, contact Research Computing and Data.
What software do I keep?
Once you graduate, you will no longer qualify to reinstall Clemson’s site-licensed software. Access to the Adobe Creative Cloud will be disabled upon graduation as well. Make sure to save copies of your Adobe files, projects and assets, or use these instructions from Adobe on how to transfer your assets to a new Adobe profile.
Can I download my submitted Canvas assignments?
Yes. Visit our CCIT Knowledge Base for step-by-step instructions.
Is there anything else I should do?
- Save a copy of your unofficial transcript after final grades are submitted. After your Username is deactivated, you will no longer be able to access your unofficial transcript—we suggest you save a copy sooner rather than later. After your Username is deactivated, you will have to request an official copy for a fee, as directed by the Registrar’s transcripts page.
- Save a copy of your tax records. After your Username is deactivated, you will no longer be able to access iRoar for your billing information. If your account is deactivated and you need to get these records, contact CCIT at (864) 656-3494.
If you have any questions or need assistance, please contact CCIT Support by calling/texting (864) 656-3494, emailing ITHELP@clemson.edu or starting a chat by clicking the orange chat box on this page.
SEO Poisoning
Have you ever searched for something on the internet using your favorite browser search engine and gotten results that are completely wrong? For example, you search for your specific car insurance company’s official website. However, the top results you see may list the name of your car company, but the website URL is not your company’s official website.
These types of results can be caused by Search Engine Optimization (SEO) Poisoning. In this type of attack, cybercriminals employ various methods to manipulate search engine results, attempting to redirect traffic to their malicious websites. On these fake websites, users may be prompted to enter their personal account credentials, which the attackers will steal, or the fake sites may include malware that is unknowingly downloaded to the user’s computer.
To avoid SEO Poisoning:
- Always visually verify links before clicking. Examine the URL carefully. Look for name misspellings or letter substitutions in the domain name. Double-check that the domain extension (.com, .edu, .gov, etc.) is correct.
- Be skeptical of the top results. Many of the first results are often “sponsored” results, meaning that they are paid to be listed first, regardless of your actual search results.
- Go directly to official websites. If you know the URL of the actual website you want, such as Amazon, then type “amazon.com” directly into the browser address bar, rather than searching for “Amazon”.

Online Holiday Shopping Tips from CCIT
 To help promote awareness during the holiday shopping season, the CCIT Office of Information Security would like to share some safe online shopping tips. Best wishes to all during the upcoming holidays!
To help promote awareness during the holiday shopping season, the CCIT Office of Information Security would like to share some safe online shopping tips. Best wishes to all during the upcoming holidays!
For more tips about staying safe online (and beyond), visit the CCIT Cybersecurity page.
Shop at secure websites that you trust
Play it safe by doing online business with trusted retailers you have shopped with before. If you are tempted to buy from a new website, research the company name before providing your payment information. When making credit/debit card payments look for website addresses that start with HTTPS and have a lock icon, which indicate a secure website.
Avoid public Wi-Fi
You might be tempted to shop online at a coffee shop or other location with free Wi-Fi. Browsing the websites may be acceptable, but do not make credit/debit card payments from a public Wi-Fi unless you have started a VPN (Virtual Private Network) session from your device. VPN creates a secure tunnel, making your data safer from interception by nearby hackers. Clemson has a free VPN you can use with your Clemson username, password and Duo authentication. You can find more information in our Services section, and if you’re using a computer, you can find step-by-step instructions in our Knowledge Base.
Create strong, unique passwords
Use a unique pass phrase for each website, and keep it private. Do not use your University password when creating accounts with online merchants.
Beware of fake delivery notifications
With packages often delayed, be wary of fake shipping alerts. Don’t click on links from delivery notification emails or texts you aren’t expecting, especially if they require “verification” from you. Visit the delivery company or vendor’s website to track your package safely.
Watch out for email scams
Holiday deals presented via email are tempting, but if the advertisement seems too good to be true, it probably is. Instead of clicking on an email link, view information directly from the merchant’s website. And don’t forget, if you get something that looks like an email scam in your Microsoft Outlook, report it to CCIT with our button.
Don’t give out too much information
Merchant websites should never prompt for your social security number. Other than your shipping address and phone number, be very wary when asked for personal information. Call the customer service line when in doubt.
Check your statements and take action immediately
Regularly check your bank and credit card statements for unauthorized transactions, and set up account activity alerts wherever possible. If you suspect a fraudulent transaction has occurred, immediately contact your bank or credit card company to report the unauthorized activity.
Know how to spot a package delivery scam
Scammers are sending fake delivery notifications claiming a package can’t be delivered, then directing victims to click a link or submit personal or payment information. These messages often look legitimate but are designed to steal credentials or financial data. Learn how to recognize these scams and always verify delivery claims through official carrier websites.
CheckIT updates to further streamline the technology governance process
Clemson University’s technology governance process, CheckIT, continues to evolve to better serve faculty, staff and researchers as they evaluate, purchase or renew technology solutions.
University employees are reminded to complete the CheckIT process before making any purchase or contract commitment. Submitting a request after a purchase has already been made can lead to delays, unplanned costs or—in some cases—inability to approve use of the product.
To help ensure timely approvals, CCIT also encourages the actual user or project owner, rather than an administrative assistant or proxy, to submit CheckIT requests. The person who will be using the software or service is often best equipped to answer the technical and usage questions that determine risk and compliance. Requests submitted by individuals without the necessary details slow down the process for everyone.
Recent updates include an expanded exceptions list, particularly benefiting faculty using free research applications on the Palmetto Cluster. If you are in doubt about whether to submit a solution for review, please reach out to itgov@clemson.edu.
Finally, campus users should begin preparing for the end-of-year freeze period in mid-December through the first week of January. New requests during this time will not be processed until the new year.
For more information, including the updated exceptions list and submission guidance, visit clemson.edu/ccit/checkit.
Shred Your Documents At A Free Campus Event
On Monday, November 17, 2025 the thirteenth annual Shred Bowl event returns to Clemson University’s campus. This document shred day is a free opportunity for Clemson staff, faculty, students and community members to bring their documents to be destroyed in a safe environment. Document shredding is another way to protect important personal information and is a strongly encouraged best practice. Please note that this event does not include official Clemson University records. Faculty and staff are encouraged to follow the guidelines from Records Management for guidance on any official University records.
This year’s event will occur in the Littlejohn parking lot between 10 a.m. and 2 pm. (219 Perimeter Rd, Clemson, SC 29634). Each vehicle is limited to three (3) boxes (copy paper box or smaller) or three (3) bags (kitchen trash bag or smaller). It is not necessary to remove binder clips, binders, paper clips, rubber bands, or staples. The image below shows where the shred truck will be located:

For more information about this year’s Shred Bowl with Shred 360 event, please visit this link.
