There has been an increase in cybercriminals using the Browser in the Browser (BitB) trick to steal login and password information. This trick has become more common on social media platforms such as Facebook and Instagram, but it can be used in any environment that uses a login page.
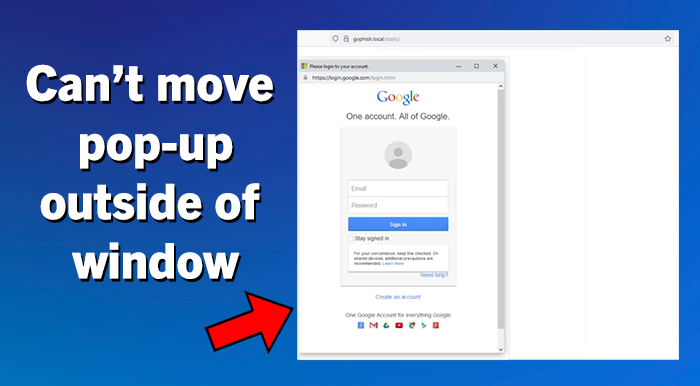
The BitB trick uses hidden code to create a fake pop-up looking window in your browser with a login prompt. Because the fake pop-up is entirely generated, it can include a convincing-looking address bar at the top that displays correct domain names. This trick can easily fool users who are looking at the URL before entering their credentials. For example, the BitB trick could be showing what looks like a pop-up window for a Google login and include the correct google.com address as well as all of the correct graphics and formatting. After entering your credentials, the user may even be redirected and logged into the official website. But through this process, the cybercriminal also collected and saved the user’s login and password information, which they can use themselves later. Most login pages are static single pages and do not typically have their login screen in a pop-up window. One of the best ways to spot this BitB trick is that the pop-up window cannot be moved outside of the original main browser window.
Ways to Avoid the BitB trick:
- For logging into any account, don’t trust a button, page link or email link.
Instead, navigate to the site’s official website URL in a separate browser tab to login. - If you are prompted to enter credentials into a login pop-up window, first check to see if the pop-up window can move outside of the browser window. Essential for the BitB trick, are iframes, which are connected to the underlying browser window and cannot be pulled outside it.
- It is also recommended to use Two Factor Authentication on any account, when available, to give you an extra layer of protection.